ThreatShield provides resilient security monitoring and defense for your IT resources through the utilization of its Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) functionalities. The use cases offered by us are crafted to secure your digital assets and elevate your organization’s cybersecurity resilience.
These application scenarios include File Integrity Monitoring (FIM) to guarantee the integrity of your vital files, Security Configuration Assessment (SCA) to strengthen your system configurations against potential threats, Vulnerability Detection to identify potential weaknesses before they can be exploited, and more. Delve into our array of use cases and capabilities detailed below.
Use cases
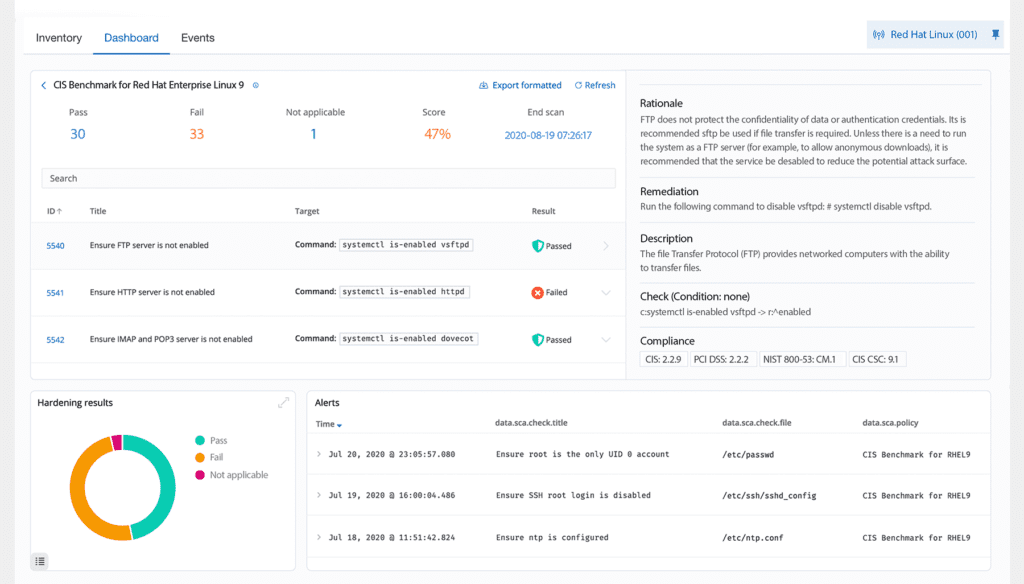
Configuration Assessment
We oversee the alignment of system and application configuration settings with your security policies, standards, and hardening guides. Our team conducts regular scans to identify any misconfigurations or security vulnerabilities in endpoints that threat actors might target. Furthermore, you have the flexibility to personalize these configuration checks, tailoring them to suit your organization's specific requirements. Security alerts not only highlight areas for improvement in configuration but also provide recommendations and references and align with regulatory compliance standards.
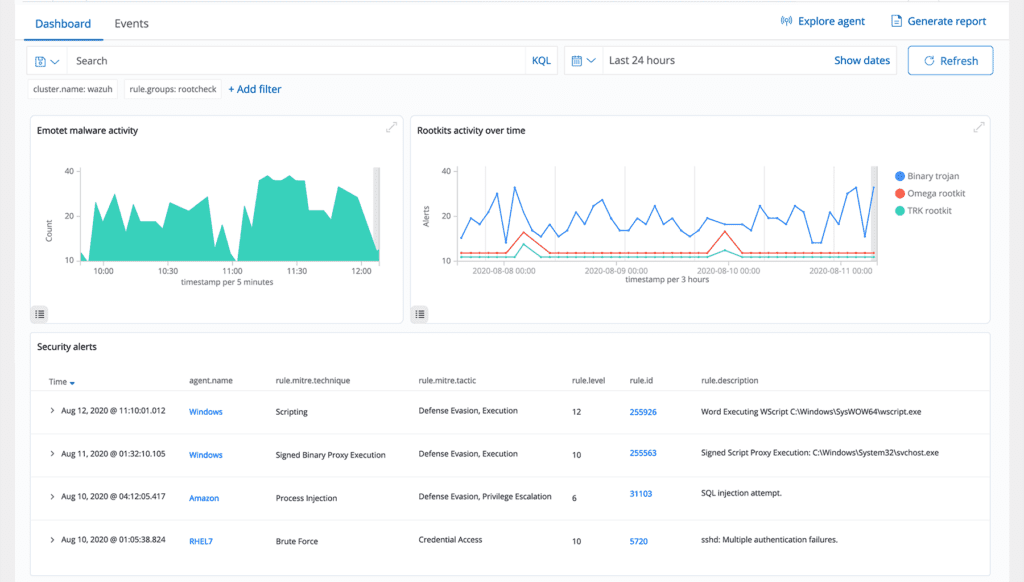
Malware Detection
We identify malicious activities and signs of compromise stemming from malware infections or cyberattacks on endpoints. Utilizing our pre-configured ruleset and features such as Security Configuration Assessment (SCA), Rootcheck, and File Integrity Monitoring (FIM), we are equipped to spot malicious behaviors and irregularities. You have the flexibility to tailor and adjust these capabilities, allowing you to align them with your organization's specific needs.
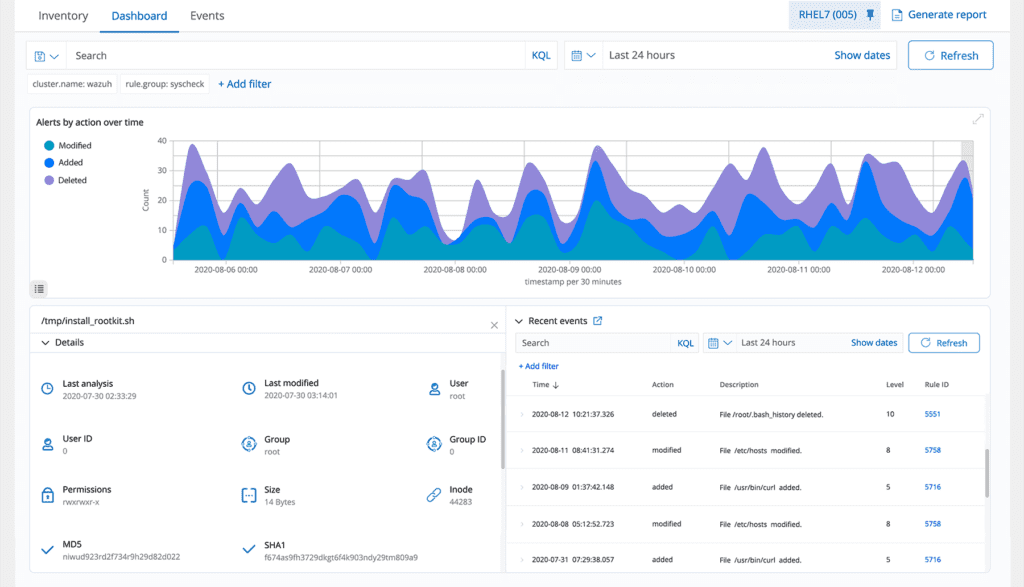
File Integrity Monitoring
We oversee the file system, detecting alterations in the content, permissions, ownership, and attributes of files that require monitoring. Moreover, we inherently recognize users and applications involved in creating or modifying files. Leveraging our File Integrity Monitoring (FIM) feature, along with threat intelligence, enables the identification of potential threats or compromised endpoints. Additionally, FIM aids in meeting various regulatory compliance standards, including PCI DSS, NIST, and others.
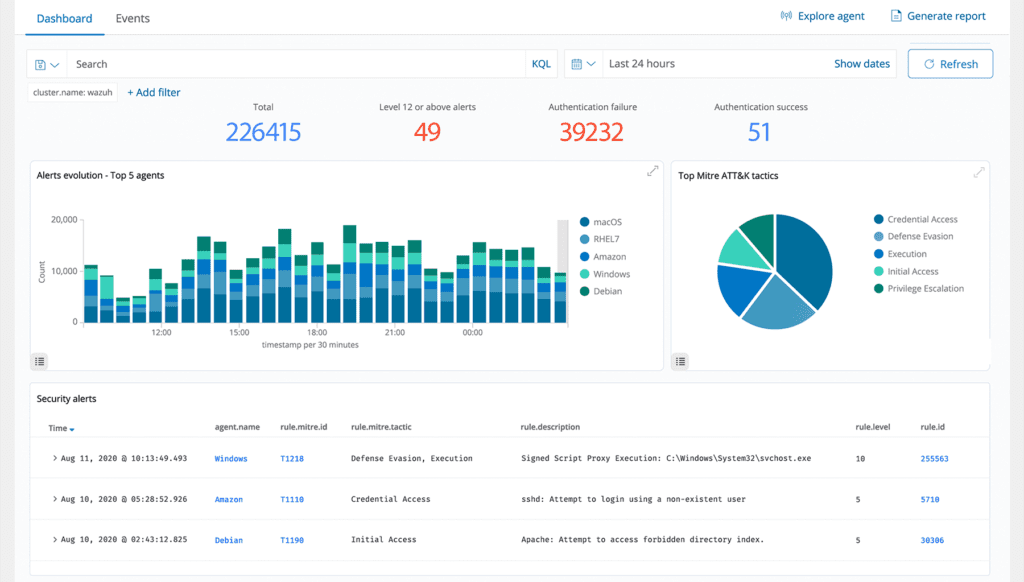
Threat Hunting
ThreatShield monitors the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep track. In addition, it natively identifies users and applications used to create or modify files. You can utilise the ThreatShield File Integrity Monitoring capability in combination with threat intelligence to identify threats or compromised endpoints. In addition, FIM helps to meet several regulatory compliance standards, such as PCI DSS, NIST, and others.
Log Data Analysis
The ThreatShield Third Eye gathers operating system and application logs, securely transmitting them to the ThreatShield server for analysis and storage based on predefined rules. These rules, implemented by ThreatShield, are designed to identify application or system errors, misconfigurations, malicious activities, policy violations, and a range of other security and operational concerns.
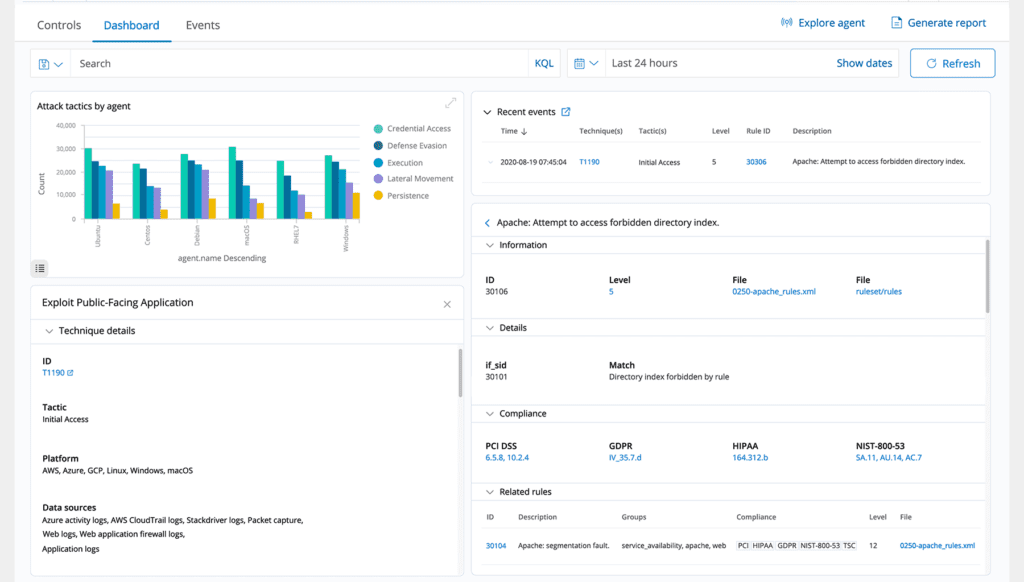
Vulnerability Detection
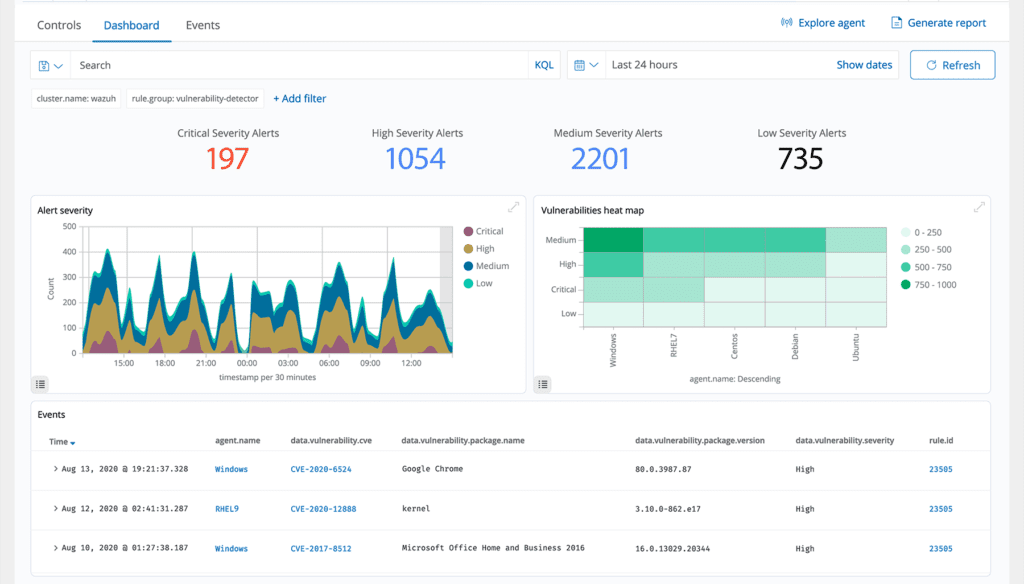
The ThreatShield Third Eye retrieves software inventory data and transmits it to the ThreatShield server. Subsequently, the gathered inventory data is cross-referenced with consistently updated CVE (Common Vulnerabilities and Exposures) databases to pinpoint known vulnerable software. This automated vulnerability detection process assists in uncovering vulnerabilities in your critical assets, enabling preemptive corrective measures before potential exploitation by malicious actors.
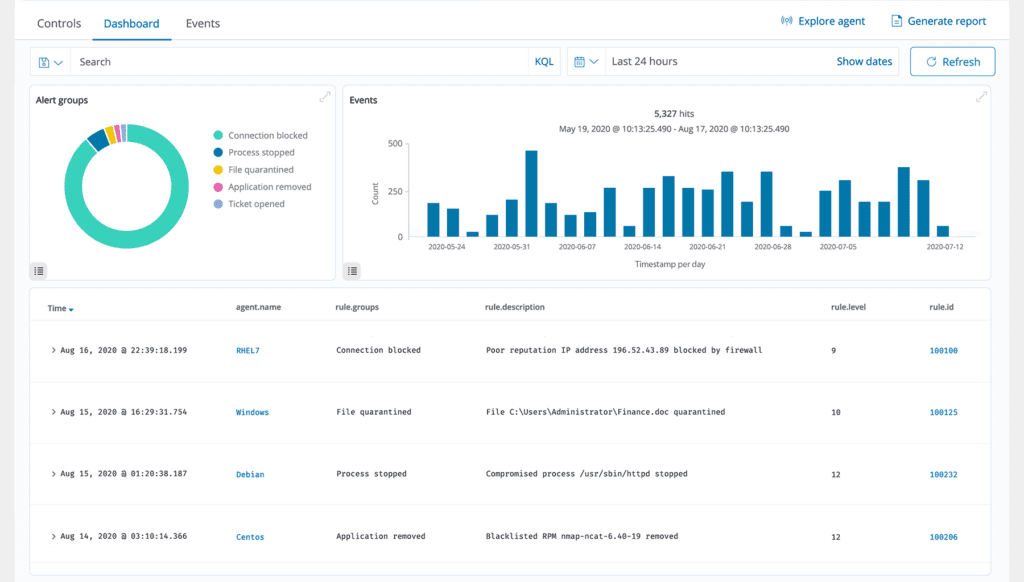
Incident Response
ThreatShield offers pre-configured active responses designed to execute diverse countermeasures against active threats. These responses are activated when specific criteria are fulfilled, encompassing actions such as restricting network access to an endpoint from the threat source and more. Furthermore, ThreatShield can be employed to remotely execute commands or system queries, identify indicators of compromise (IOCs), and assist in carrying out incident response tasks.
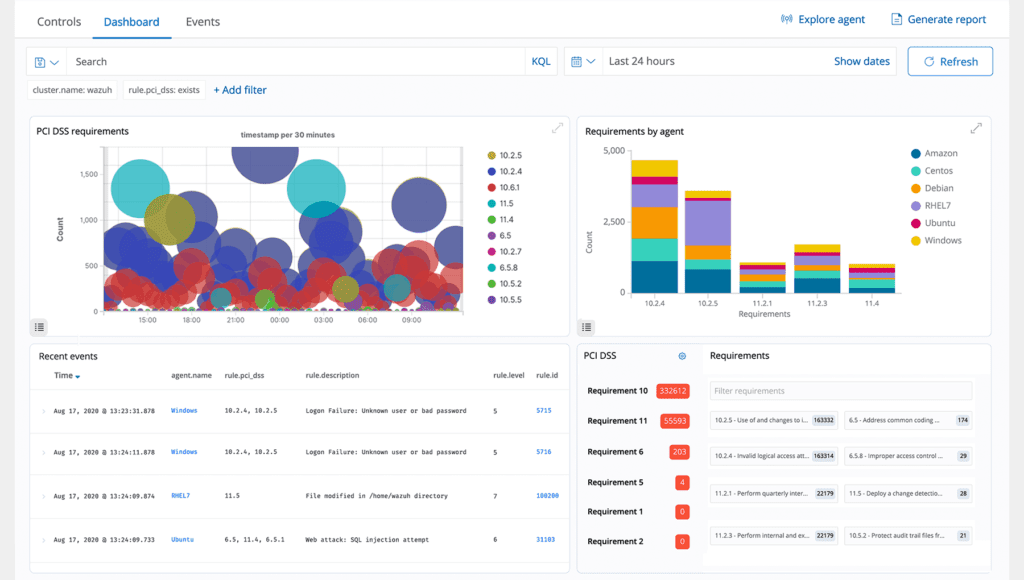
Regulatory Compliance
We offers essential security controls required for achieving compliance with industry standards and regulations. These controls encompass features like File Integrity Monitoring (FIM), Security Configuration Assessment (SCA), vulnerability detection, system inventory, and more. By integrating these capabilities with its scalability and multi-platform support, ThreatShield assists organizations in fulfilling technical compliance requirements. Additionally, ThreatShield furnishes reports and dashboards tailored to regulations such as GDPR, NIST, TSC, and HIPAA.
IT Hygiene
ThreatShield constructs a current system inventory encompassing all monitored endpoints. This inventory includes details such as installed applications, running processes, open ports, hardware and operating system information, among others. Gathering this information aids organizations in enhancing asset visibility and upholding sound IT hygiene. Complementing these efforts, various other ThreatShield capabilities, including vulnerability detection, Security Configuration Assessment, and malware detection, contribute to safeguarding monitored endpoints and promoting improved IT hygiene.
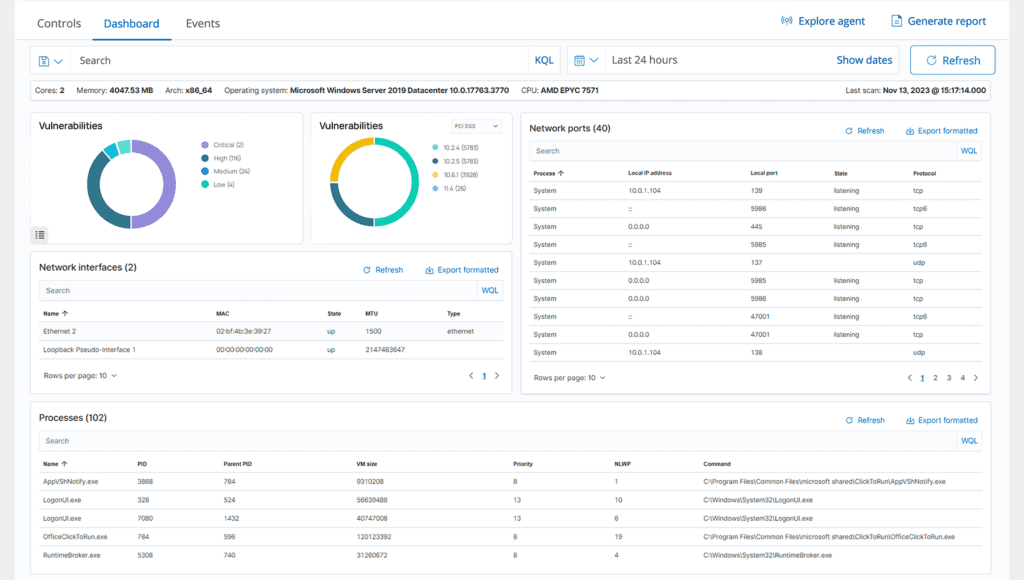
Containers Security
ThreatShield offers enhanced security insight into Docker hosts and containers by observing their activities and identifying threats, vulnerabilities, and irregularities. The ThreatShield Third Eye seamlessly integrates with the Docker engine, enabling users to oversee images, volumes, network configurations, and active containers. Continuous collection and analysis of comprehensive runtime data by Threatshield include alerts for scenarios like containers operating in privileged mode, vulnerable applications, the presence of a shell within a container, modifications to persistent volumes or images, and other potential threats.
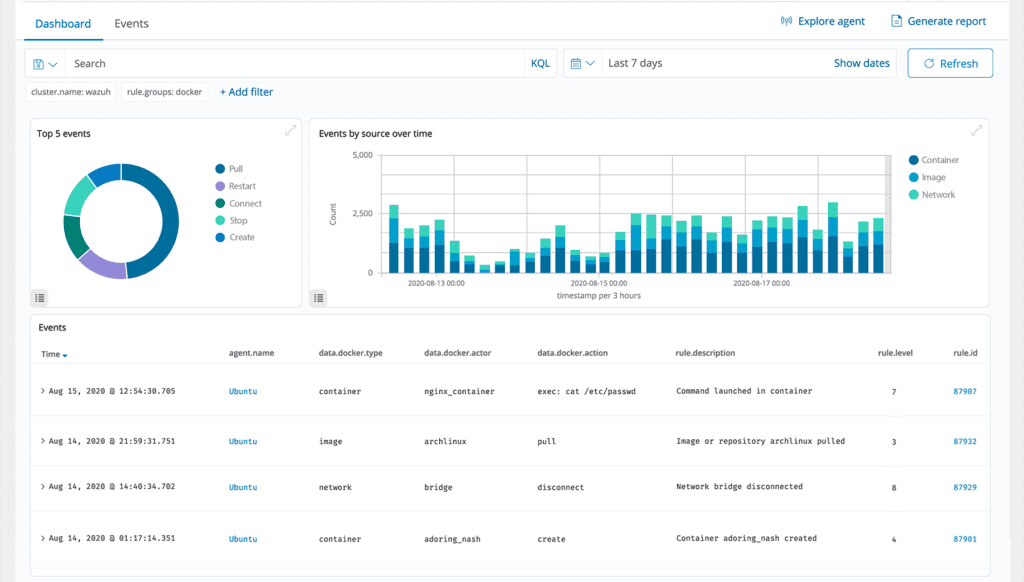
Posture Management
ThreatShield integrates with cloud platforms, collecting and aggregating security data. It alerts on discovered security risks and vulnerabilities to ensure security and compliance with regulatory standards.
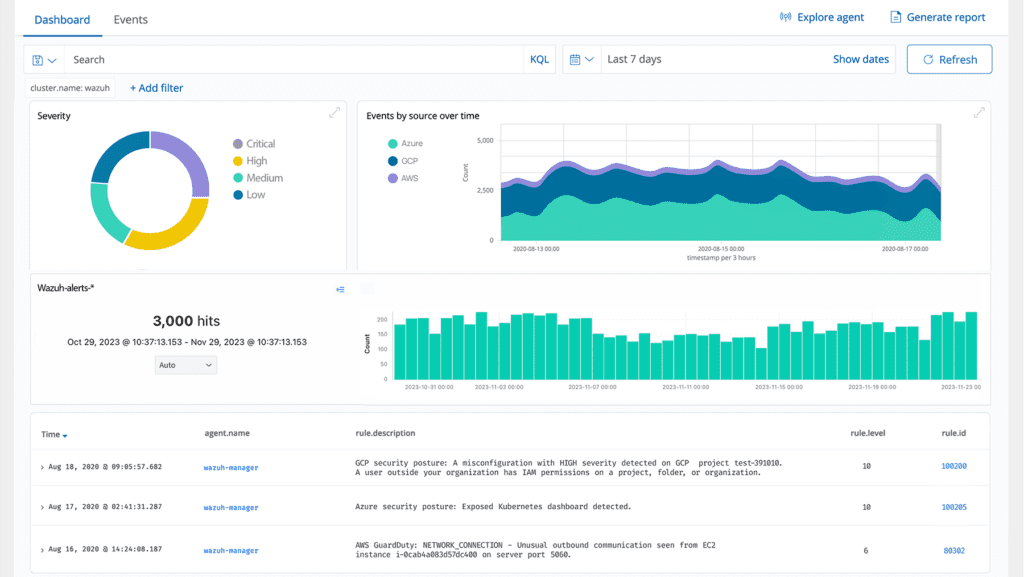
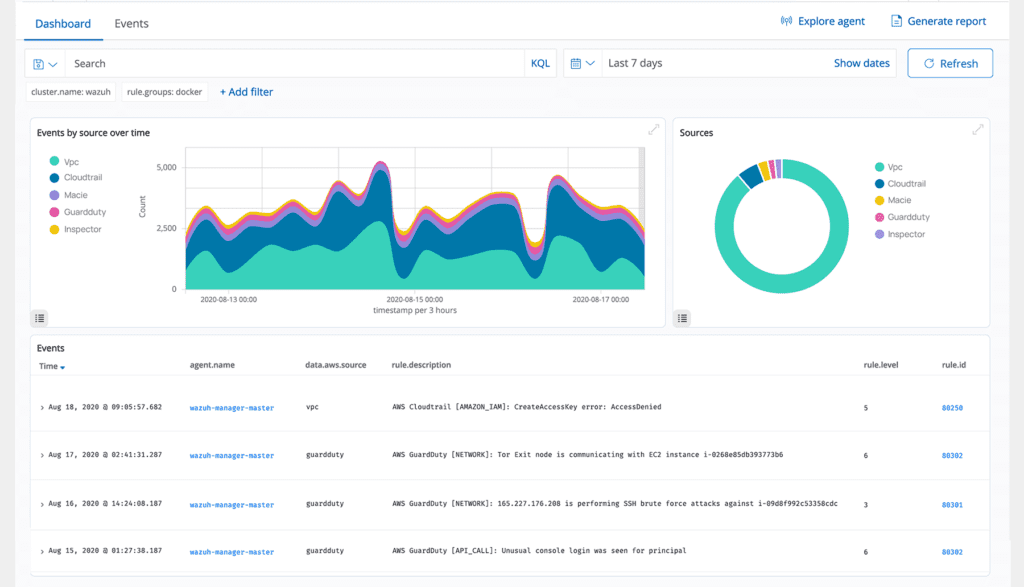
Workload Protection
ThreatShield safeguards workloads across cloud and on-premises environments. Its integration capabilities extend to popular cloud platforms such as AWS, Microsoft Azure, GCP, Microsoft 365, and GitHub, facilitating the monitoring of services, virtual machines, and activities within these platforms. ThreatShield's centralized log management is instrumental for organizations utilizing these cloud services, ensuring compliance with regulatory requirements.
Explore ThreatShield, the comprehensive security platform
Explore a distinct solution, an open-source cybersecurity platform that uniquely combines SIEM and XDR capabilities.
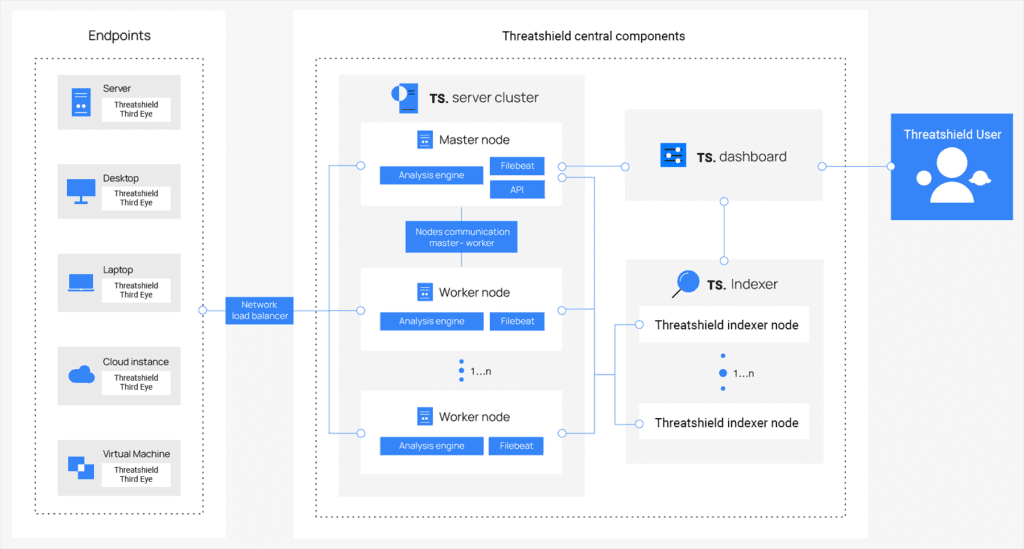
Central components
ThreatShield Indexer
The indexer functions as a remarkably scalable full-text search and analysis engine tasked with indexing and storing alerts generated by our server. Its installation can be tailored to suit specific environmental requirements, accommodating either a single-node configuration or a multi-node cluster.
ThreatShield Indexer
The server manages the Third Eye, configuring and updating them remotely when necessary. This component analyzes the data received from the Third Eye, processing it through decoders and rules and using threat intelligence to look for indicators of compromise.
ThreatShield Indexer
An adaptable and user-friendly web interface designed for data mining, analysis, and visualization. The dashboard serves as a tool for overseeing ThreatShield configurations and monitoring its current status.
Discover how ThreatShield
can assist your organization
Explore the ways ThreatShield enhances organizational security with its robust features, ensuring proactive threat prevention and efficient incident response. Uncover the power of ThreatShield in fortifying your digital defenses and safeguarding critical assets.











